Understanding Dot1x Port-based Authentication
What is Dot1x Port-based Authentication
IEEE 802.1x (802.1x) is a standards-based approach for providing port-based network access.
802.1x is a layer2 protocol that defines how Extensible Authentication Protocol (EAP) frames are encapsulated.
802.1x also defines hardware components, such as the figure below:

Supplicant: PCs, laptops, other devices that support 802.1x standard.
Authenticator: Catalyst Swicths, Access Points, …
Authentication Server – Radius Server: Microsoft Radius servers, Cisco secure ACS, …
Authentication Process
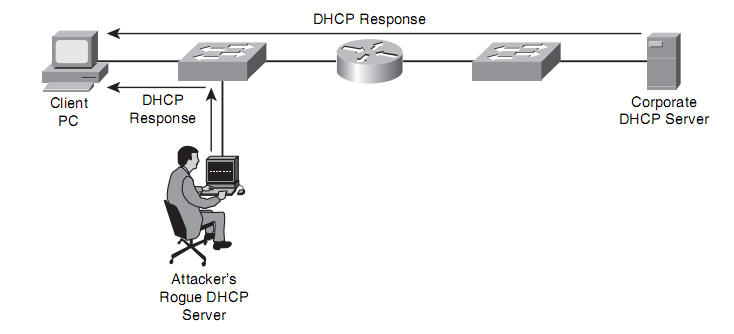
Let’s consider the figure below:

Step1: When boots up or pluged-in to the switch, the 802.1x-enabled PC initially sends a Extensible Authentication Protocol over LAN (EAPOL) request.
Step2: The switch that configured 802.1x receives the request and reply with a challenge.
Step3: The PC sends its credentials, such as username/password.
Step4: The Switch forwards these credentials to the authentication server – Radius server.
Step5: Radius Server validates Credentials. Upon that verification, the switch grants the PC access to the network or not.
Switch Ports Authorization state
In 802.1x environment, the physical switch port that has the PC connect to devides to 2 logic ports: a controlled port & an uncontrolled port.
The uncontrolled port is the only port over which PC can send traffic until it is authenticated. This uncontrolled port passes only EAPOL, CDP and STP traffic.
After the PC is authenticated, the physical switch port opens its controlled port, overwhich PC can send user data.
If the PC is configured for 802.1x but the switch is not, the PC fails to receive the EAP traffic from the switch. So the PC acts as if it has been authenticated and begin transmits its user data.
Conversely, the switch considers that the PC does not have credentials. So the switch does not grant network access to the PC.

During IEEE 802.1x authentication, depending on the switch port state, the switch can grant a client access to a network. We can control the port authorization state by using dot1x port-control interface configuration command with the keyworks:
- Force-authorized: This is the default setting, which means that there’s no 802.1 authentication.
- Forced-unauthorized: This option causes the switch ports to remain in the unauthorized state.
- Auto: this is the most common setting. This option causes the switch ports to participate in 802.1x.
802.1x Host Mode
We can configure an IEEE 802.1x port for single-host mode or for multiple-hosts mode.
Single-host mode: only one client can be connected to the 802.1x-enabled switch port.
Multiple-hosts mode: multiple hosts can be connected to the 802.1x-enabled switch port. In this mode, if a single host authenticates, the port transitions to the authorized state, allowing all other hosts access to a network. We can combine 802.1x and port security to manage the network access.
Extensible Authentication Protocol
IETF said:
This document defines the Extensible Authentication Protocol (EAP), an authentication framework which supports multiple authentication methods. EAP typically runs directly over data link layers such as Point-to-Point Protocol (PPP) or IEEE 802, without requiring IP. EAP provides its own support for duplicate elimination and retransmission, but is reliant on lower layer ordering guarantees. Fragmentation is not supported within EAP itself; however, individual EAP methods may support this.
EAP may be used on dedicated links, as well as switched circuits, and wired as well as wireless links. To date, EAP has been implemented with hosts and routers that connect via switched circuits or dial-up lines using PPP [RFC1661]. It has also been implemented with switches and access points using IEEE 802 IEEE-802]. EAP encapsulation on IEEE 802 wired media is described in [IEEE-802.1X], and encapsulation on IEEE wireless LANs in [IEEE-802.11i].
One of the advantages of the EAP architecture is its flexibility. EAP is used to select a specific authentication mechanism, typically after the authenticator requests more information in order to determine the specific authentication method to be used. Rather than requiring the authenticator to be updated to support each new authentication method, EAP permits the use of a backend authentication server, which may implement some or all authentication methods, with the authenticator acting as a pass-through for some or all methods and peers.
So, EAP is not a specific authentication mechanism. It’s an authentication framework. EAP provides some common functions and negotiation of authentication methods, called EAP methods. There are about more than 40 EAP methods which are clearly defined in IETF document. Some most-used methods include EAP-MD5, Cisco LEAP, EAP-FAST, Protected EAP (PEAP), EAP-TLS.
Configure and Monitoring IEEE 802.1x
Step1. Enable AAA on Catalyst Switch
Aaa new model
Step2. Enable 802.1x Authentication
Aaa authentication dot1x default group radius local
Step3. Optionally configure Authorization
Aaa authorization network default group radius
Step4. Configure the Switch to communicate with the Radius Server
Radius-server host 10.0.0.1
Radius-server key keyhere
Step5. Globally enable 802.1x on the Catalyst Switch
Dot1x system-auth-control
Dot1x guest-vlan supplicant (optionally configure the support of Guest Vlan )
Step6. Configure 802.1x on an Interface
Switchport mode access
Dot1x port-control auto
Dot1x host-mode multi-host (optionally configure 802.1x to operate in multi-hosts mode)
Dot1x guest-vlan 100 (optionally configure Guest Vlan)
Dot1x auth-fail vlan 200 (optionally configure Restricted Vlan)
Step7. Verify the configuration
Show dot1x
Show dot1x fa0/1
Show dot1x statistics interface fa0/1
Show aaa servers